This
tutorial is over one of the most well-known DNS enumerators named
Dnsenum. Dns enumeration is conducted in active information phase to
obtain as much detailed information as possible regarding target
system. Before getting into DNS enumeration process, it is highly
important to know the basics of how DNS servers work. I highly
recommend you having enough knowledge on things like Zone Transfer
and DNS record types to better understand the concept. It is safe to
say that obtaining crucial information about a target can sometimes
be pretty easy when a server is misconfigured so that you can easily
find out its reverse DNS records, name records, the mail server they
use even operation system installed on a target system. Anything can
be found with this technique might have critical vulnerability to
exploit and help you get into the system. There are a bunch of
practical tools that help you gather information about DNS records.
DNSrecon, fierce,dnstracer and dig would be a few of these. This
tutorial is particularly about DNSenum.
To
use the tool you should execute it in the console typing dnsenum.
When it comes up you’ll see its parameters. You can see the most
used ones down below. Each one has a description in the help menu. So
you can try out other ones yourself.
--enum
It contains three
different commands which are threads, max subdomain number and whois
query options. Thread value set to 5, second option is for the number
of subdomains scraped from Google which is set to 10 and last but not
least it has whois query which you should optionally enable with -w
parameter.
--noreverse
As it says itself in
the help menu, it skips the reverse lookups.
-f
This
is for bruteforcing. There needs to be the directory of the wordlist
file includes subdomain names. You should or use the built-in
wordlist in /usr/share/dnsenum/dns.txt either find a better one on
the Internet.
-o
It
can output the results in xml format. I think this function is sort
of buggy for this version. It doesn't give proper formatted reports.
When I tried converting one into pdf format, online converter gave me
a 312 pages long pdf file. Most of pages were blank.
-w
For
performing whois queries on c class network.
--dnsserver With this parameter, you can indicate what dns server you would like to use for your
enumeration. It works with Google unless you specify a DNS server.
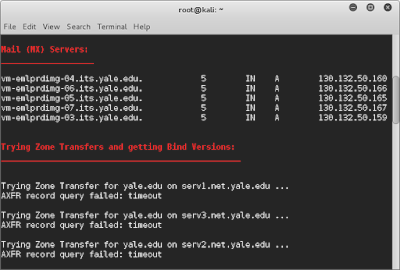
This
time I run it for a website (zonetransfer.me) that is purposefully
misconfigured with zone transfer. It gives us all information with
record types of this server.
You
would better compare the result you get from dnsenum with the ones
obtained with an another tool to make sure you do not miss anything
important.